December 5th, 2025 by admin
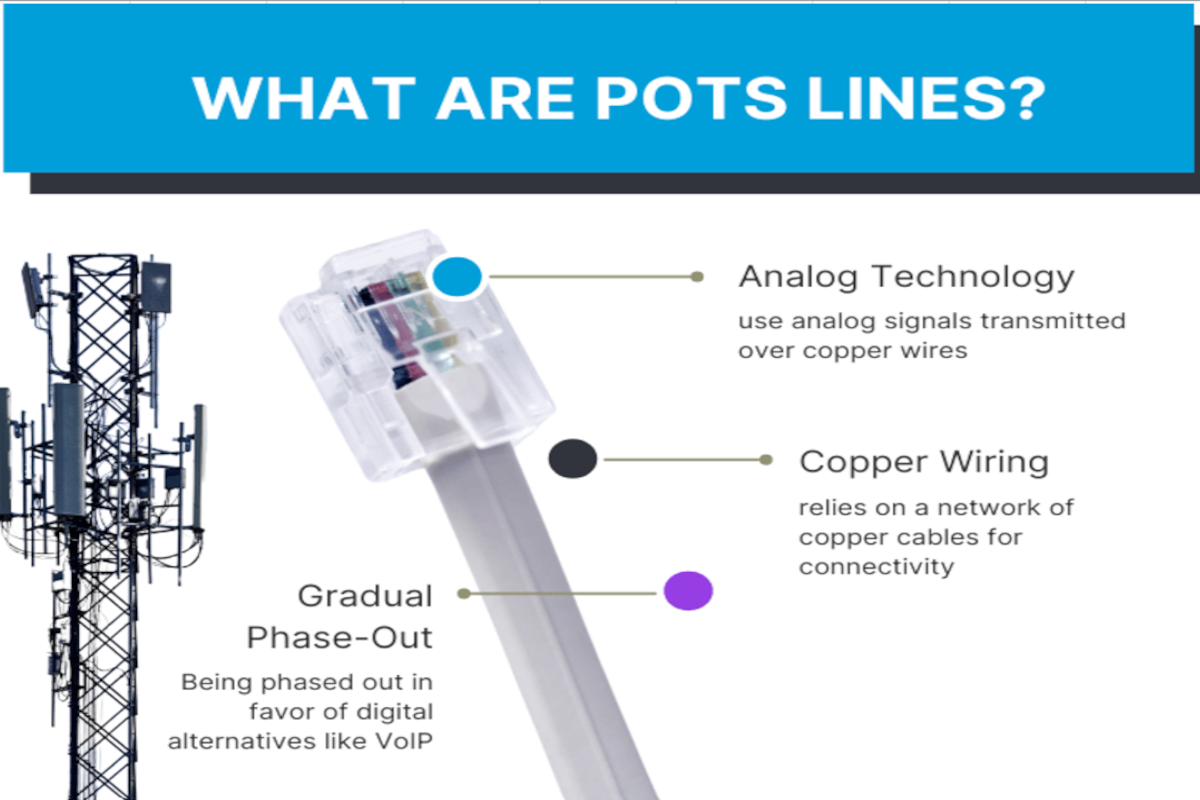
For decades, POTS (Plain Old Telephone Service) lines have powered essential building systems—fax machines, fire alarms, security panels, elevator phones, gate access systems, and more. But today, organizations relying on these legacy analog lines...
Read Full Story »
Tags: best connectivity, business phone system, phone lines
Posted in: Phone System
December 1st, 2025 by admin
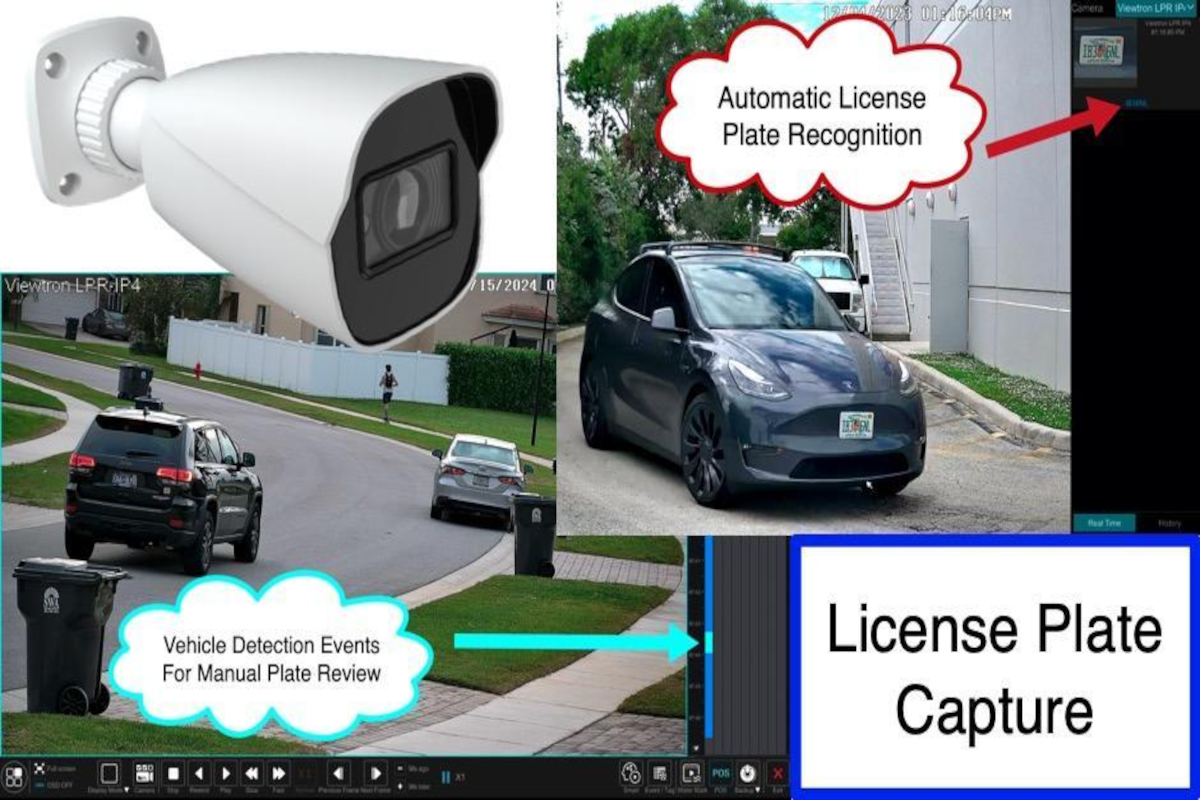
Security threats are evolving—and so should the way we protect our businesses, communities, and properties. Traditional cameras are valuable, but they often fail to deliver the level of detail necessary to identify vehicles, track incidents, and...
Read Full Story »
Tags: cameras, protect my data, video surveillance
Posted in: Security
November 20th, 2025 by admin
Automating Expense Reporting for Business Efficiency
Managing business expenses can feel like a never-ending chore. Receipts pile up, spreadsheets get messy, and approvals drag on. Meanwhile, your employees wait for reimbursements and wonder whether...
Read Full Story »
Tags: best practices, business continuity, expanding business, technology solution
Posted in: IT Solutions
November 13th, 2025 by admin
Why Is the Private Cloud Regaining Traction?
Hybrid cloud strategies that blend the best of public and private environments give businesses the flexibility they need. Not every workload belongs there, though.
As organizations evolve their cloud infrastructure...
Read Full Story »
Tags: backup, best practices, cloud
Posted in: Cloud Computing (Hosting & Colocation), Communications
November 6th, 2025 by admin
How a Routine HP Update Went Off the Rails
HP's OneAgent software is a background tool that manages systems and firmware updates across HP devices. Earlier this month, HP released version 1.2.50.9581 of the software, which included a cleanup script...
Read Full Story »
Tags: data storage, disaster prevention, microsoft
Posted in: Security, Telecommunications
October 30th, 2025 by admin
What Happened in the Prosper Data Breach?
Prosper Marketplace confirmed that attackers gained unauthorized access to its systems, which contain the personal user information for millions of customers. While the company has not disclosed the exact...
Read Full Story »
Tags: data backup, network protection, network security
Posted in: Data Backup & Disaster Recovery, Cyber Security
October 23rd, 2025 by admin
IT: The Unsung Hero of Everyday Efficiency
IT is the backbone of every successful business. With smart technology for business efficiency in place, things run smoothly.
But the wheels start to come off the bus when systems are outdated or poorly...
Read Full Story »
Tags: best practices, network communications, productivity
Posted in: Business Solutions
October 16th, 2025 by admin
OAuth App Attacks Explained
OAuth is a convenient and widely trusted technology that allows users to access applications using accounts like Google or Microsoft. It eliminates the need to type a password.
In OAuth application abuse cases, threat...
Read Full Story »
Tags: backup, communication, network protection
Posted in: Cyber Security
October 9th, 2025 by admin
Customers Expect Convenience
Today's customers expect instant access to information and immediate options for action. From reserving a dinner table to scheduling home repairs, people prefer companies that allow them to book appointments anytime,...
Read Full Story »
Tags: business communications, technology solution, technology
Posted in: Solution
October 2nd, 2025 by admin
The Paper Problem: Why "Old School" Isn't Always Efficient
Paper has a certain comfort to it. It feels familiar, dependable, and easy to manage. That is, until it's not.
Think about how much time your team spends printing, filing, scanning, or...
Read Full Story »
Tags: best practices, data, efficiency
Posted in: Technology
September 25th, 2025 by admin
What Happened in the Mango Data Breach
According to Mango, the customer data exposure occurred after attackers accessed systems belonging to an external marketing partner. The company said certain customer information was accessed, including:
...
Read Full Story »
Tags: backup, best practices, business continuity
Posted in: Cyber Security
September 18th, 2025 by admin
Have you ever lost an important document at the most inopportune moment? It's frustrating and can cost your establishment time, money, and trust.
The latest Microsoft Word file recovery feature makes it easier than ever to retrieve unsaved or lost contracts,...
Read Full Story »
Tags: business communications, microsoft, network
Posted in: Solution
September 11th, 2025 by admin
From Cash Register to Command Center
Older POS systems basically serve as cash drawers with credit card readers attached. But times have changed.
Today's point of sale software is not only smarter and faster; it can handle significantly more than...
Read Full Story »
Tags: expanding business, network, productivity
Posted in: POS
August 28th, 2025 by admin
Optimizing Your Infrastructure: Data Center Cabling Best Practices
Reliable cabling is often the unsung hero behind seamless data center performance. Whether you're constructing a new facility or upgrading an existing one, following best practices now...
Read Full Story »
Tags: best practices, cabling, data center
Posted in: Business Solutions, Informative, Guides
June 17th, 2025 by admin
Have you ever wondered how secure your business’s social media accounts really are? Cybercriminals are getting bolder, using well-known brands like Google to lull people into a false sense of security. Understanding how the average phishing scam works...
Read Full Story »
Tags: data, phishing, security
Posted in: Cyber Security
June 16th, 2025 by admin
Can your establishment defend itself against a cyber attack? The recent Dior data breach shows that cybersecurity is not optional in today’s digital world. Learn more about it here.
When Luxury Brand Cybersecurity Measures Fail
Dior Fashion and Accessories...
Read Full Story »
Tags: data, hackers, security
Posted in: Cyber Security
June 14th, 2025 by admin
How confident are you in your security whenever your team operates on the web? Browser extensions, while useful, can introduce vulnerabilities you might not notice right away.
Future versions of Google’s browser might remove Chrome admin privileges to...
Read Full Story »
Tags: data, security
Posted in: Cyber Security
June 13th, 2025 by admin
Few innovations have had a more significant impact on how companies operate, grow, and adapt than cloud computing. Once a cutting-edge luxury, cloud scalability is now a must-have for any company trying to remain competitive.
What Is Cloud Computing...
Read Full Story »
Tags: business solutions, Business, cloud services, cloud solutions
Posted in: Cloud Computing (Hosting & Colocation)
June 12th, 2025 by admin
When trying to grow your business, your customers and employees are equally important. They’re the heart and soul of everything you do. Building a lasting business means keeping both groups happy, and help desk automation can play a big role in that...
Read Full Story »
Tags: helpdesk, productivity
Posted in: Support
June 11th, 2025 by admin
Security researchers report a new threat facing businesses that could put your data, as well as its backups, at serious risk. They’ve discovered that ransomware gangs exploit Kickidler in new attacks, meaning that they’re weaponizing your company’s tool...
Read Full Story »
Tags: hackers, ransomware
Posted in: Cyber Security
June 10th, 2025 by admin
Working from home used to be pretty rare. Most people still dealt with daily commutes, office cubicles, and morning traffic. But when the pandemic hit, companies had to adapt fast, and that shift changed the way we work, probably for good.
Thanks to...
Read Full Story »
Tags: remote office, remote workforce
Posted in: Business Solutions, Collaboration & Conferencing, Communications
June 9th, 2025 by admin
New research from cybersecurity firm Cofense serves as a serious wake-up call for businesses: AI-powered phishing attacks are not only becoming more frequent, but they’re also far more convincing and effective than ever before.
These aren’t the typical...
Read Full Story »
Tags: data, hackers, phishing
Posted in: AI, Cyber Security
June 7th, 2025 by admin
How prepared is your establishment against ransomware attacks? The recent breach of LockBit, one of the most notorious digital criminal groups, has shed some light on the shadowy world of cybercrime. Keep reading to learn more.
Who Is LockBit?
Jon DiMaggio,...
Read Full Story »
Tags: hackers, ransomware
Posted in: Cyber Security
June 6th, 2025 by admin
What would happen if your sensitive company data were no longer secure? That’s the risk we face as quantum computing advances.
This emerging technology, while groundbreaking, has the potential to compromise traditional encryption methods. Learn why businesses...
Read Full Story »
Tags: data, technology
Posted in: Cyber Security
June 2nd, 2025 by admin
Procuring new software, applications, or devices for your business is always exciting. You and your team will be rearing to take advantage of all those features. Still, you have to know that they’re secure.
Is there a chance your new installation contains...
Read Full Story »
Tags: data, hackers
Posted in: Cyber Security